For the last four months, Cofense security experts have noticed a new way of phishing attacks. This new campaign allows the attackers to deliver emails with QR codes, in order to spoof Microsoft security notifications. The most notable target of the campaign turns out to be a major US Energy company.
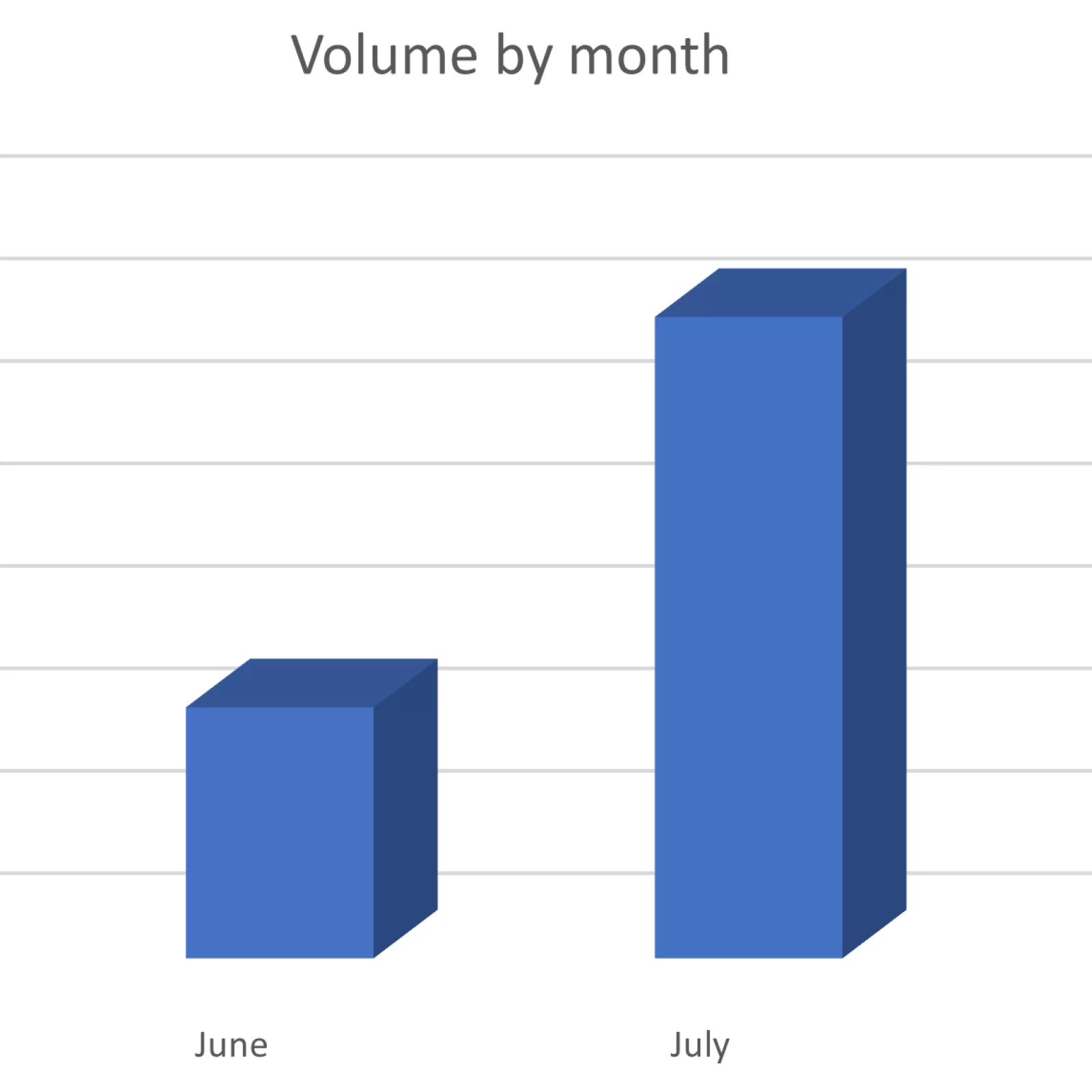
The campaign has been running for several months, from May to August. Most of the attacks were in July, and even 29% of the 1000 emails reviewed in the campaign were sent to an American energy giant. Attackers hope to bypass protection by inserting a QR code into mail. The assessments of security experts are, however, that this is a test campaign, in which QR codes are tested as an attack vector.
What is the nature of the attack?
By default, the attacker sends an email message to his victims. According to the contents of the message, the user is being urged to upgrade the Microsoft 365 account. A PNG or PDF file with a QR code is attached to the message, and the trick is to have the user scan the image for the purposes of verifying the real owner of the account.

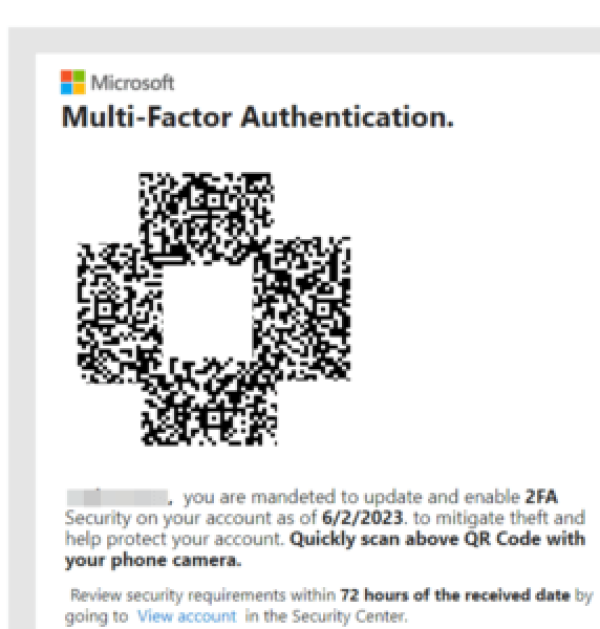
The invitation is written in such a way so that there’s a sense of urgency and that the steps are mandatory; otherwise, the company cannot be held accountable. Ironically, the request in the email is for double-authorization of the profile, which is supposed to make the account of the user more secure!
Why QR links?
Attacks that take advantage of QR codes are not common, so they can bypass automatic security measures. The QR code hides malicious addresses. If these addresses were part of a normal email and not hidden in a QR code, they would have been instantly detected and blocked by the protection of most email providers.

The QR Code attack is more devious. Most of the phishing links were Bing redirect URLs, but other notable domains include krxd[.]com (associated with the Salesforce application), and cf-ipfs[.]com (Cloudflare’s Web3 services). Second part of the string is actually a redirect to Microsoft 365 phishing website.
‘Abusing trusted domains, using obfuscation tactics, coupled with hiding the URLs inside QR codes embedded into a PNG or PDF attachment, helps ensure that emails bypass security and make it into inboxes.’ states Cofense.