In the past few weeks, many people received SMS messages with information about a shipment that cannot be delivered. The message includes a link that redirects the users to a web page where they are asked to enter their personal data and, most importantly, payment information, in order to deliver the package again to the “correct address”.
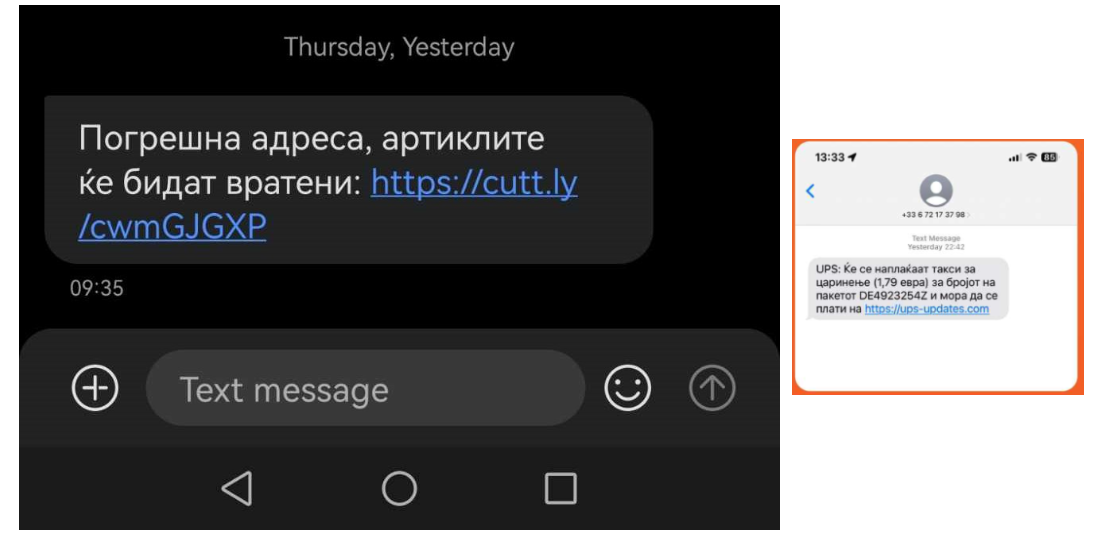
What is the real purpose of these messages?
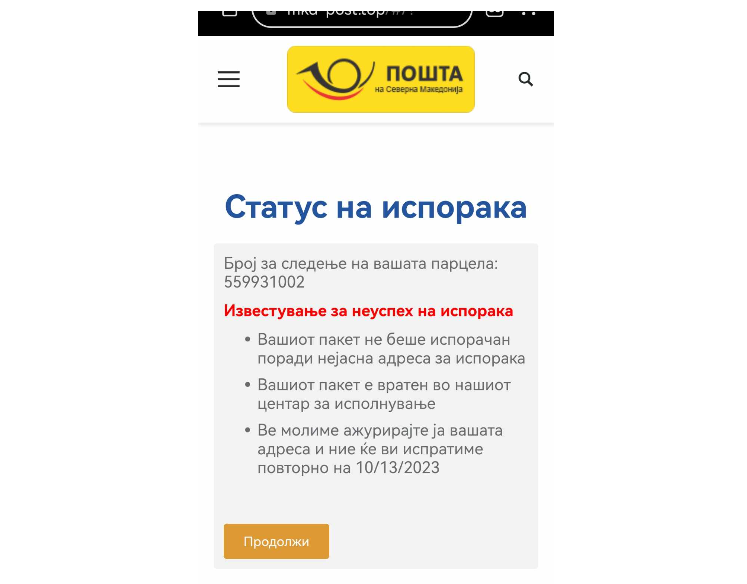
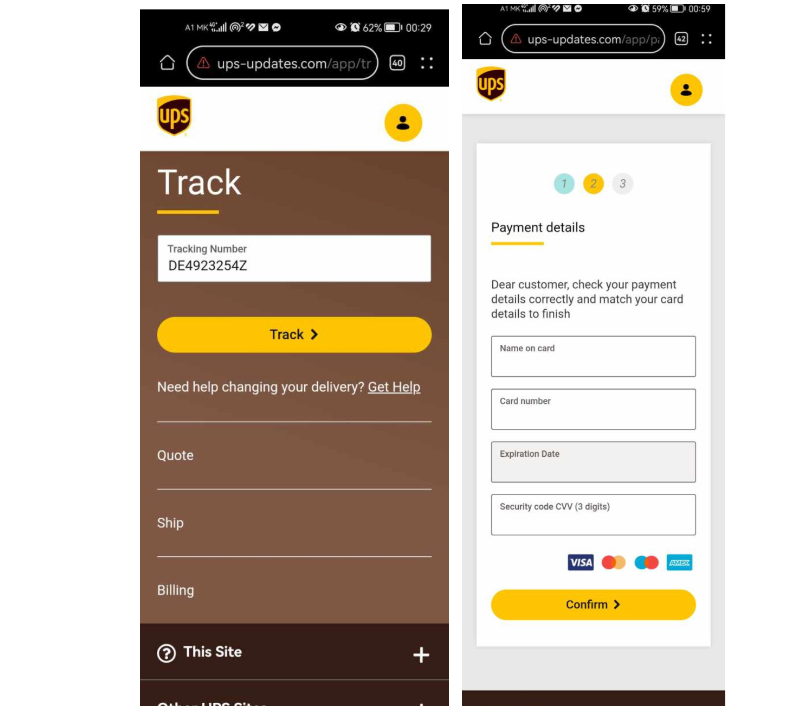
This activity is a typical example of smishing attacks, that is, the attackers created a fake website of Poshta na Severna Makedonija, with a logo and design similar to the national post office. The link found in the content of the message redirects to this website and then asks to enter personal and payment card data from which a certain amount of money would later be charged.
We have written about such national smishing scams before, like the one for the IRS.
Citizens receive various links, usually masked through URL shortening services like Linkr.it, which actually mask the real domain.
For example, one of the messages we analyzed has the domain:
https://linkr.it/3j90aT which actually redirects to: https://za.ousez.3-a.net/bill which opens this page:
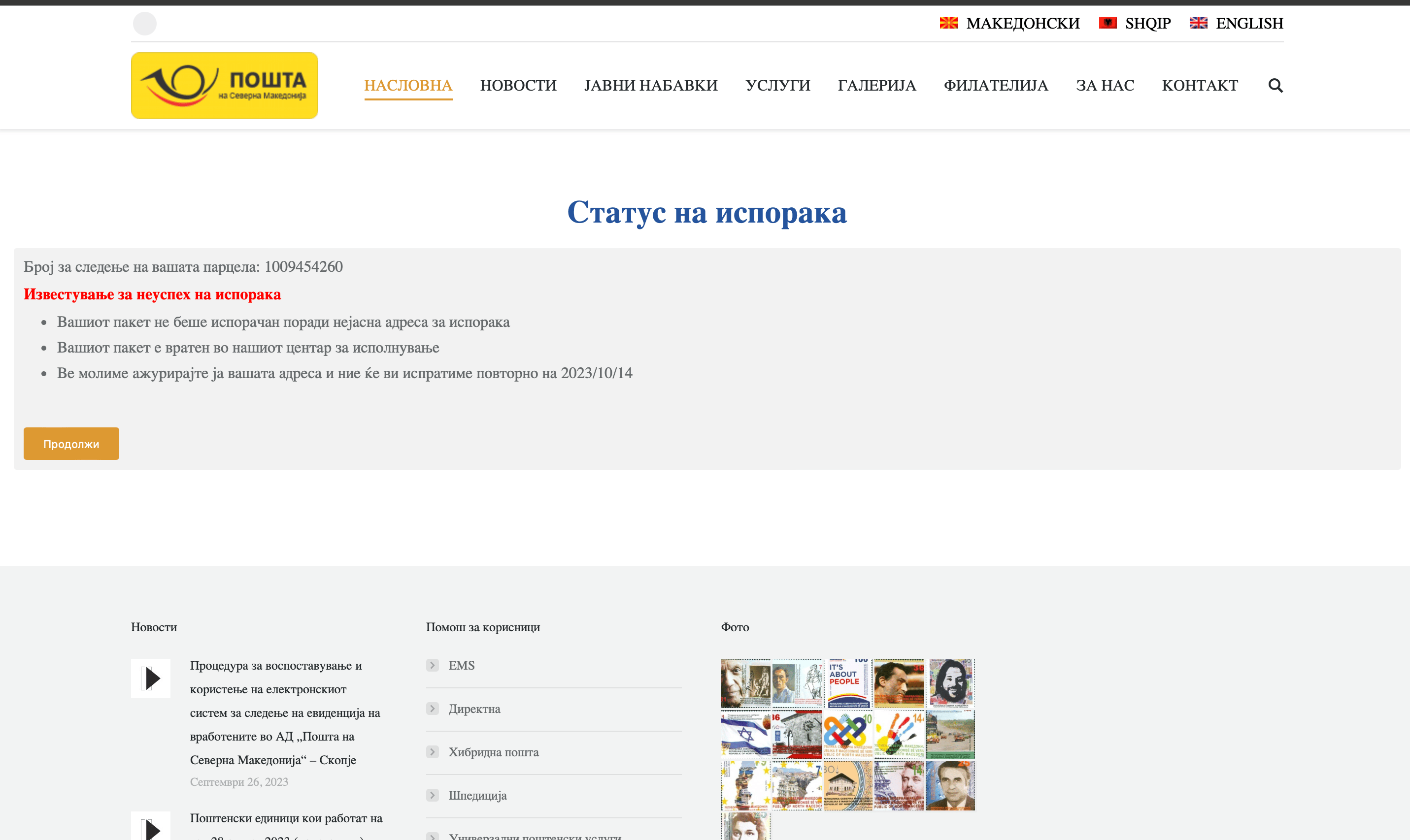
This page is identical to the official page of Macedonian Post, that is, it contains the same header and footer.
Checking the domains that are involved in fraud usually leads to a dead end because either hacked servers and sites are used, or the domains are falsely registered, but in certain cases they are also with protected WHOIS data.
For example, the TLD domain from the above-mentioned site is 3-a.net, whose WHOIS data is:

From this it can be seen that the domain is hosted on the ChangeIP.com service and is registered through the same valid dynamic DNS service, and fraudsters use this legitimate ChangeIP service to easily change the destination of the domain. Most likely ChangeIP’s fraud reporting system depends on someone sending a report initially for them to respond, ie it is reactive rather than proactive.

This means that ChangeIP or other such services (such as those for shortening URLs) will respond for an account or domain, only in case of previous registration. Just imagine how many frauds would have been prevented if there was a responsive CIRT team that would immediately react and report domains and abuses to the appropriate services to take the necessary steps.
An additional interesting fact is that the attack was designed and targeted towards the Macedonian population because a large part of the rotating domains use specific terms such as mkd-post, makposta, postamk, etc…
A practical example:
There is a high probability that you are waiting for a shipment, you are at work or in a hurry, you receive an SMS message of the type that there is a certain problem with the delivery. You click on the link and do not pay attention to the domain, SSL certificate, etc. If you are not tech-savvy, it is even more likely that these things mean nothing to you, and you will not pay any attention or suspect that something is fishy.
In an instant, you will enter your personal data, and then the payment card data – because the amount needed to solve the specific problem is only 50–60 denars. Not everyone would fall for this, but surely there would be someone who can’t afford to pay more attention…
According to unofficial information, i.e. writings of people on social networks, the amount that was charged to the victims was in most cases much higher than 50–60 denars.
What is phishing, and what are the many types of this form of an attack?
Phishing refers to cyberattacks in which attackers, through fake web pages, try to extort personal data, payment card data, login information for a certain system, etc.
- Email Phishing: Attackers send emails that contain links that lead to web pages that require the input of certain sensitive data. This is the most common form of phishing.
- Phishing via text messages, known as smishing (the word is actually a combination of SMS and fishing): Attackers send SMS messages that contain links that lead to web pages that require the entry of certain sensitive data.
- Vishing (voice phishing): Attackers call by phone and pretend to be someone else, all in order to extort certain sensitive data. It is a common case where fraudsters call elderly people that their children have been in an accident, and they urgently need money.
- Pharming: Attackers redirect traffic from a real website to a fake website; and the rest is history!
How to protect yourself from such attacks?
The most effective solution to protect against such attacks is to be very careful and not to rush to enter sensitive data (especially payment card data) on a platform. In case you are scammed, and you find out about the same in a short time, get in touch with your bank, as you may have the option to block the transaction or take other appropriate measures. Additionally, you can learn how to recognize which websites are real and which ones are fake… and for that, you can start here.
BONUS
As of this writing, the link that was sent via SMS at 09:25 on 12/10 redirects to the same website, but the design and language of the content have changed – meaning they are now targeting Uruguayan citizens with the same scam:

This tells us about the seriousness and effectiveness about the whole operation and how they target different countries in just a few minutes.
The suspicious thing about this whole situation, like the one with the IRS, is that the scammers have a list of a huge number of valid numbers that most likely comes from some hacked database. For now, it is difficult to claim where such data could come from, but there are doubts on all sides.